May 30, 2013
Source:http://www.extremetech.com/extreme/156922-quantum-encryption-isnt-as-unbreakable-as-you-think
In theory, we’ve had this licked for hundreds of years. We’ve long known how to create totally unbreakable encryption, ciphers so strong that no amount of modern supercomputing power could brute force its way into your grocery list, if you really desired to stop it: just garble it all to hell. That’s really all it takes, and the processes involved in doing so are simple, quick, and easy enough for anyone to use. There really is no flaw on the theory side at all — yet the realities of actually implementing these theories have frustrated everyone from spy agencies to note-passing school children. When it comes to cryptography, the proof is definitely in the pudding.
Take, for a moment, the simplest possible form of encryption, in which you want to keep information solely to yourself. You don’t need to transmit any key or alternate cipher-text to anyone, removing the single greatest challenge in cryptography, and yet there are still impossible problems. Can you memorize a sufficiently long and perfectly random key for encrypting and decrypting your self-message, preferably a key that’s just as long as your sensitive information itself? If not, then you must store the key somehow, and immediately introduce a glaring security vulnerability. And you certainly can’t generate a truly random sequence off the top of your head, which introduces another chink in the armor. Do you move your lips silently as you go through your cryptographic routine? Could someone have a camera to look over your shoulder as you copy out the intermediate steps? Could someone use classified brain-scanning technology to grab the encryption process straight out of your mind as you practice it?
This Stanford invention helps handle entangled photons, but does it introduce vulnerabilities in the process?
If we can’t devise a practically invulnerable form of encryption when we don’t even need to transmit a message, how could we possibly hope to create an invulnerable form of real communication? Quantum cryptography is often referred to as “perfect” encryption, but this is just shorthand for its cutting-out of the most classically insoluble problem in cryptography: key transmission. There are still a host of other possible vulnerabilities, and now researchers are beginning to find the cracks even in quantum crypto’s single most ballyhooed feature.
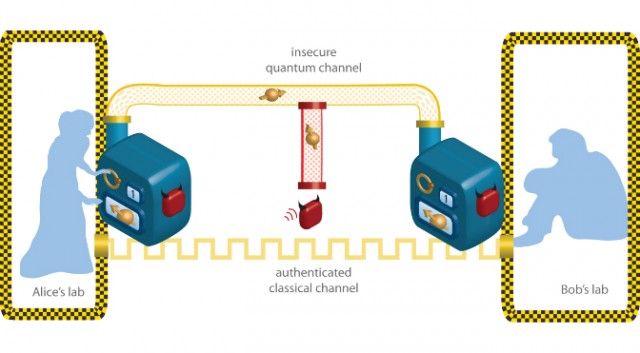
Though the term “quantum cryptography” is thrown around rather loosely, these days it mostly refers to the idea of quantum key distribution, taking a truly random key that transforms every letter (or number, or whatever) in a sensitive message in a truly unpredictable way, and uses the quirks of quantum physics to get the key from sender to recipient with no chance of interception. Sometimes quantum teleportation comes up as a means to distribute this key, but more often (and more plausibly) the solution has to do with the unobservable nature of entangled particles; it’s not so much that a key can’t be intercepted, but that it can’t be intercepted without alerting the intended recipient.
In this way, quantum cryptography has always relied on many of the same dubious assumptions as all other forms of cryptography: that both parties are totally trustworthy, that their local encryption and decryption processes are totally secure, and that their equipment does not introduce some flaw that can be exploited to get around our beautiful, useless theoretical bulwarks. In their attempts to actually quantify the practical failure rate of quantum cryptography, a team of researchers led by Renato Renner of the Institute for Theoretical Physics in Zurich, have detailed several such possible failings in technology. For instance, transmitters can send multiple instances of a photon which should be totally unique, allowing one instance to be read by an eavesdropper and other to go undisturbed.
Though we won’t know this particular group’s estimates of the failure rate for quantum cryptography until they announce their findings next month, whatever specific value they come to is less important than the simple fact that the number is not 1.0; the point that needs to be made, but that should always have been assumed to be true, regardless, is that quantum cryptography is not perfect cryptography, and never will be. Its security relies on the same imperfect principles as any other form of secret communication, things like the imperfect nature of human engineering, of human attention, and of human loyalty.
And, of course, we can’t dismiss the possibility that quantum theory might just be wrong. Maybe there really is a way to observe a quantum bit without disturbing it; it’s a small chance, but one that must be heeded all the same.